- April 18, 2025
- Posted by: Interwest Communications Team
- Categories: News, Uncategorized

Originally posted on May 8, 2021 @ 10:34 am

The Remote Work Security Checklist
Setting up a remote work policy at your business can be a challenge, especially when it comes to security. It helps to have a security plan, and building a plan is a lot easier with a useful checklist on hand. For over 30 years, Interwest Communications has been helping businesses stay secure by providing access control, alarm systems, and video surveillance. We’ll give you a rundown of the remote work security checklist to help keep businesses safe and secure.
The Primary Security Issue: Remote Work
The most common security issue in a workplace is remote work. When you have employees working from home or on the move, whether it’s with personal devices or an issued device, that is a data security risk. Many businesses had previously opted to exclude remote work opportunities to mitigate security risks and associated costs in the past, but the pandemic has changed the landscape.
“We see an incredible 42 percent of the U.S. labor force now working from home full-time. About another 33 percent are not working – a testament to the savage impact of the lockdown recession. And the remaining 26 percent – mostly essential service workers – are working on their business premises. So, by sheer numbers, the U.S. is a working-from-home economy. Almost twice as many employees are working from home as at work.”
To stay afloat, businesses were forced to quickly adapt their technology and workflow to allow employees to remotely perform their jobs, with as little disruption to operations as possible.
Prioritize Data Security for Remote Workers
Remote access is a tool to access the network from an offsite location. It is usually applied in businesses when people work from home, or move between many locations. Remote access points are another point of access for malware and thus another point that needs security measures in place.
Before, remote work was considered a security risk, and the increased usage of video conferencing applications has highlighted those concerns. Zoom has many known security issues, and the need to protect a network and work calls from intrusion has become vital.
In the absence of a secure and centralized computer network, businesses need to be explicit about how employees are expected to handle confidential business data. You need to make a plan. During the COVID-19 pandemic, remote work was likely initially seen as a temporary measure. However, when employers see the advantages of working remotely and can put procedures in place to support employees, it will become a viable way for companies to continue operating in the future and will offer employees more flexibility.
Security Planning For Employers
Now is the time to revisit your company’s data privacy and security policies to ensure they are relevant to the new remote-working environment. If you don’t have any data privacy or security policies, now’s the time to create these documents. Here are important policies to include:
- Rules about using personal devices for work purposes, preferably issuing work devices to all employees rather than using a BYOD (bring your own device) policy.
- Guidelines on automatic device locking and password protection.
- Only allowing the use of approved applications, devices, and websites.
- Two-factor or multi-factor authentication protocols.
- Creating and maintaining VPNs to encrypt sensitive data.
- Privacy policies: your company’s privacy policies may need updating if your employees are accessing or processing personal information in new ways.
- Terms and conditions for secure use
- Device hardware standards
- Password management, including minimum password standards.
- A data breach policy integrated into your IT security policy or available as a separate document. This policy should help your employees respond to the loss or theft of company data.
You should ask your employees to review these documents regularly. All this documentation should be revisited and revised as time goes by for greatest security integrity.
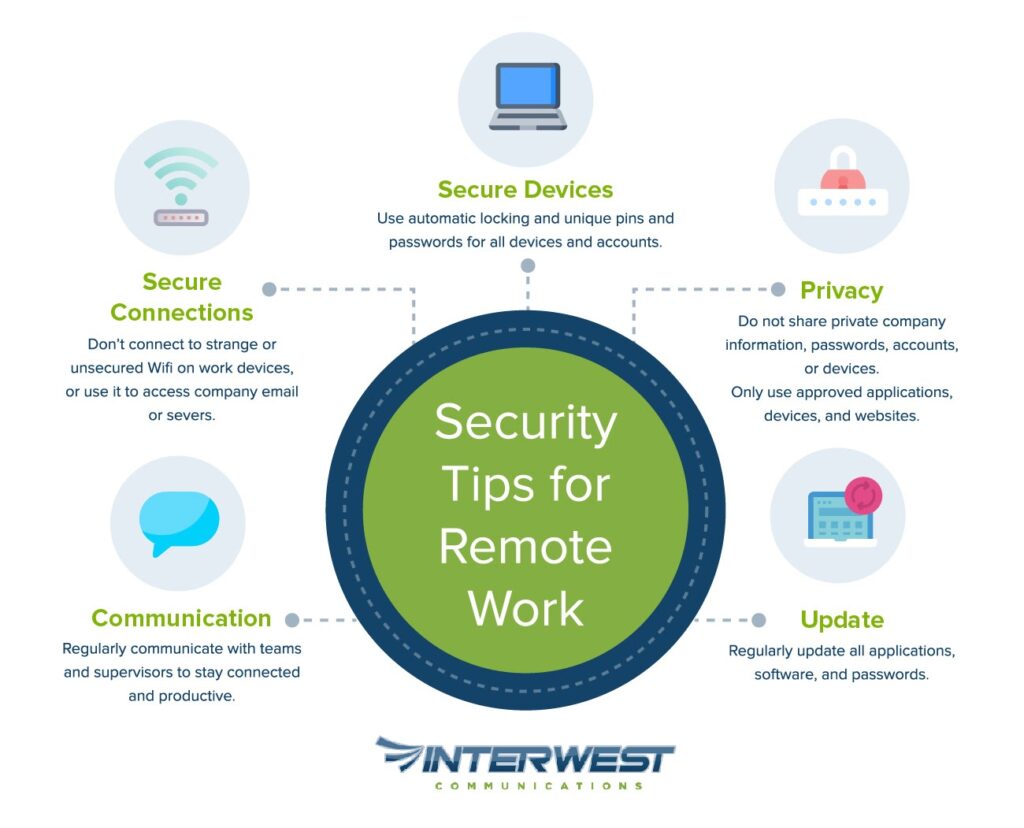
Security Planning For Employees
The user is an important line of defense in business network security, by making sure they understand how to identify and avoid threats. When you’re setting up a series of guidelines or rules for employees, these are some good plans and procedures to include:
- Do not share private company information, passwords, accounts, or devices.
- Use automatic locking and unique pins and passwords for all devices and accounts.
- Do not respond to emails, SMS, or social media messages unless the employee is sure that the sender can be verified.
- When receiving an email from an unknown sender, do not click on links or download attachments.
- Check for the “padlock” symbol in your browser address bar when visiting a website.
- Don’t connect to strange or unsecured Wifi on work devices, or use it to access company email or severs.
- Regularly update all applications, software, and passwords.
- Regularly communicate with teams and supervisors to stay connected and productive.
This, coupled with the network security technology checklist, will ensure remote work security.
Network Security Threats Employers Should Educate Employees About
A business’s security is more than a lock on a door and an alarm on the windows. In the digital world, the internet is a vital utility through which business is conducted, and therefore network security should be of the utmost importance. However, many businesses aren’t fully aware of all the threats to their network security, and the severity of the risk of damages and losses they pose.
Threats to a business’s network and data can come in many different forms, and not understanding those threats is the first security risk that businesses need to understand. Network security threats are always changing and adapting, and it’s important to be familiar with them to be able to protect against them.
Threats can enter a business’ network through a number of vulnerabilities. The best way to mitigate threats and the risks they pose is to understand them and know how to prevent them.
Malware
Malware is malicious software intended to steal information and damage devices. It spreads through websites and phishing schemes, and often enters a system because someone inadvertently invites it in. Several healthcare companies were hit with malware and ransomware in 2020, and the results were catastrophic for both the companies and their customers.
How to prevent malware:
Detection systems and employee education on recognizing and mitigating potential threats.
Viruses
Like their biological counterparts, computer viruses are corrupted applications, files, or web links that replicate themselves and spread to corrupt more data. They can result in widespread destruction and damage to systems, opening them to further vulnerabilities. Viruses can also result in losses and damages due sensitive data and assets being compromised.
How to prevent viruses:
Anti-virus software, firewall, and employee education on recognizing and mitigating potential threats.
Phishing
Phishing schemes target businesses via email. They attempt to elicit sensitive or personal information with false rhetoric and introduce malware. Unlike viruses, spyware, ransomware, and malware, phishing schemes are social in nature, with employees or other stakeholders inadvertently giving access to a system.
How to prevent phishing:
Educating employees and having protocols dictating the sharing of information are essential to preventing phishing attacks.
Spyware
Spyware is a type of malware specifically designed to enter devices and track internet usage and data. Cybercriminals use the information from tracking to extract further sensitive data for monetary gain.
How to prevent spyware:
Anti-spyware software, firewall, and employee education on recognizing and limiting access.
Ransomware
Ransomware is malware that digitally extorts a business by blocking their access to essential files or systems until they pay a ransom or meet demands.
How to prevent ransomware:
Anti-virus software installed on all devices, firewalls, and employee education.
The Network Security Technology Checklist
The first thing to think about is your network security infrastructure. This infrastructure includes the hardware and software that make up the network, and protect it. Below are the biggest issues that we encounter among businesses as they grow, and what’s important to make sure remote work remains secure.
Firewall Protection
Firewalls are a barrier that monitors and filters traffic. Their express goal is to prevent suspicious or malicious entities from entering the network. Ensuring that your company has a properly set up firewall can ensure that you’re protected from any incoming and outgoing network traffic that could also result in the costly loss of private data, exposing employee information, or even losing trade secrets. While your business is hopefully immune from these high profile threats, it’s important to understand that hacking by domestic and foreign groups, and even foreign governments is a very real threat.
Intrusion Prevention System (IPS)
Intrusion Prevention Systems actively detect and block network security threats. Coupled with your firewall, IPS ensures that your network is protected from external issues.
An IPS sits behind your firewall and adds an extra layer of analysis that can help flag threats and dangerous actions. Better still, this builds on older IDS systems. IPS actively analyzes your network traffic flow to highlight issues.
Antivirus & Anti-Malware
Installing antivirus software on all devices to protect from malware corrupting a network and stealing data is an essential part of maintaining the security of your company. Nothing can be more dangerous than a large number of company owned devices with no security solution in place. This can expose sensitive client and company information. Worse still, you could even become exposed to a ransomware hacker group, and get stuck with a massive bill, or lose your data. A best case scenario is that devices become unusable, but more often, you might find that your business suffers financial damage and long term reputation issues that dog you for years.
Email Filters
Email filters prevent spam with potential threats from entering your email. It’s important to set specific rules for what a filter does and does not allow into the network for effective security. There are many services that provide email filtering. Things to consider when selecting a filtering service are:
- Accuracy – An email filter isn’t effective if it’s not accurate. If it lets spam into your inbox, but sends important emails from colleagues to the trash, it is both a security risk and a real inconvenience.
- Compatibility – Compatibility affects how well a filter can recognize threats. Incompatible applications can cause operational interference on both sides. That interference could result in lost email functionality as well as security effectiveness.
- Customization – Every business and business network is different and has unique needs. More customization allows for more control. More control means it’s easier to filter out what you don’t want and keep what you do want.
Security Software
Security software protects specific platforms against threats targeting them. Devices and applications can have specific vulnerabilities. Specific security softwares addresses those vulnerabilities without interfering with other operations. These security softwares are a layer of security in a specific area, in addition to the blanket security measures.
- Wireless Security – Wireless networks are expanding, and so are opportunities for malware to enter a wireless network.
- Mobile Security – Mobile devices are being used more by businesses, and more malware is being released to target them.
- Web Security – The web is a wide open space that allows for different technology to connect. This is also a way for malware to find its way into a network, so web security makes sure that you’re not exposed to it.
- Application Security – As more applications are used, more forms of malware are created to target them. It’s essential to secure them.
Secure Network Devices
Each device on a network is another component to secure. It is important to make sure that all security measures are applied to each device. All devices on your network are using Wi-Fi Protected Access 2 (WPA2). WPA2 uses complex security certifications to secure wireless access. Network Devices to Secure Include but are Not Limited to:
- Routers – Connects a network through a wide-area network (WAN) or a local area network (LAN). Routers use protocols to communicate and funnel data through the best route. Routers either use wireless or a wired connection.
- Switches – Create a network and allow devices to communicate.
- Hubs – A type of switch that forwards all network traffic to every device. It connects Ethernet devices via many ports.
- Gateways – Link two or more networks by translating the signals/protocols of different networks.
- Servers – Devices designated to receive, store, and distribute data across devices.
Remote work was previously considered a huge data security risk because it can be difficult to implement the necessary security technologies and protocols across the span of remote workers. Usually, businesses could manage every aspect of their network with monitoring, and network configuration, but remote work limits those capabilities. Call2Teams helps solve the remote work security problem.
Call2Teams for Remote Work Security
Call2Teams is a secure and accessible application that integrates remote work and modern video collaboration into your current infrastructure, that allows employees to travel and consistently engage with their managers and teams.
Call2Teams is Secure
Call2Teams is fully secure and approved for use on leading PBXs. Previously, remote work was considered a security risk, and the increased usage of video conferencing applications in the pandemic augmented those concerns. Zoom has many known security issues, and the need to protect a network and work calls from intrusion has become vital. Normally you’d have to deal with setting up firewalls, anti-virus applications, a private network, and cabling.
But, with Call2Teams, businesses can extend their secure and centralized computer network with encrypted data transfers, antivirus software, and multi-factor identification to remote workers. A service like Call2Teams paired with quality security protocols, will help you make sure that work keeps running smoothly without intrusion or interruption.
Virtually Connect with Call2Teams
Call2Teams allows you to enjoy modern video conferencing on any device, and remote work collaboration without disrupting your current hardware setup, or initiating any costly updates. The software utilizes existing phone numbers and hardware systems while adding in remote video and collaboration through Teams on PC, Mac, and mobile. Once set up, you can manage the entire system from an easy-to-use web portal, including managing security across the network and multiple devices.
Call2Teams is Easy to Use
Call2Teams is convenient, centralized, and accessible. Everyone knows what a nightmare new technology adoption can be, especially with a diverse workforce with different levels of experience and technical know-how. It’s absolutely essential for a thriving workplace to have tools and equipment that are easy to use, so everyone can focus on work. Interwest Communications goes above and beyond to ensure that all the training and assessment needs for new tech are met, so your business doesn’t experience security risks and significant downtime.
Save time on training for all new systems, and headaches for IT departments with a simple cloud service. Avoid the hassle of dealing with multiple new systems across many different devices on remote networks, by integrating the current infrastructure with new technology, and manage them from one convenient centralized access point. Our team can work with you to assess your existing set up, and painlessly complete the integration process without a lapse in security.
Interwest Has You Covered for Remote Work Security
If this guide is raising some alarm bells for you and your organization, it might be time to start considering a more robust security solution. Interwest Communications can help. Video conferencing technology is more important than ever for remote workers to feel engaged and supported, and remain productive during pandemic isolation. Interwest is here to help business owners keep data secure and employees connected during these uncertain times with video communication and collaboration technology that allows them to get their work done and securely connect into existing infrastructure. We have the knowledge and experience to secure and streamline your network and communications. Get in touch with us today to get started.
