- July 30, 2020
- Posted by: Interwest Communications Team
- Categories: News, Uncategorized


Choosing the Best Security System for Your Business
Every business needs a high quality security system to protect their assets while also being protected from damages to property and reputation.
When choosing the best security system for your business you should consider three main factors:
- Cost
- Scalability
- Type of assets you need to protect
The last one is key to picking the right security system for your unique business needs. If you’re looking to protect physical assets, data, or people in your organization, you’re going to need a n can address each need. We’ll take you through the process of choosing the best security system, as well as understanding what they do along the way.
What is a security system?
The basic security system consists of one or more sensors to detect intruders, and an alerting device to indicate intrusion. However, a typical premises security system includes the following components:
-
PCUs & ACPs
The premises control unit, alarm control panel, or simply the panel, is the brain of your security system. It reads sensor inputs, tracks the status of a system as either armed or disarmed, and signals intrusions. In modern systems, this is usually one or more computer circuit boards inside a metal enclosure with a power supply.
-
Sensors
Sensors are devices that detect intrusions. They may be placed at the perimeter of the protected area, within it, or a combination of both. Sensors use a variety of methods to detect intruders, such as by monitoring the opening and closing of doors and windows, or by monitoring unoccupied interiors for motion, sound, or vibration.
-
Alerting Devices
Alerting devices are also known as alarms. They signal alarm, usually in the form of bells, sirens, or flashing lights. They serve the dual purpose of warning of intrusion and scaring off burglars. They can also be used to warn occupants of fire or gas.
-
Keypads
Keypads are small devices that function as the human-to-machine interface that connects to the alarm system. Keypads often have indicator lights, a display, or both.
-
Connection Components
Connective components are components that wire everything together to the control unit. More modern systems use wireless communication.
-
Monitoring Service
A monitoring service is contacted in the event of an alarm, where operators at the station can see the signal and take appropriate action, including contacting the property owners, notifying the police, or dispatching security forces. Signals from monitoring services can be transmitted via a dedicated alarm circuit, telephone lines, or the internet.
5 Types of Security Systems & Areas of Security for Businesses
1. Video Surveillance
Video surveillance systems use the internet or closed-circuit televisions (CCTV), and cameras to monitor their premises, and are an essential part of intrusion prevention and security systems. One of the benefits of video surveillance is that in the event that the security measures fail to prevent losses or damages, there will be a record and evidence of the events that took place, which makes resolving damages easier with authorities, insurance companies and interested parties.
Video surveillance systems are effective to protect physical property, assets, and people at any time, and are suitable for businesses of any size with physical properties to secure.
Video surveillance systems can consist of up to 3 parts:
- Video surveillance cameras
- Video recorder(s)
- POE switch(es) for certain types of recorders
Which video surveillance system is best for my business?
The important details when selecting a video surveillance system for your business’s security system are considering the cost and the scalability in comparison to the value of your physical property.
Larger organizations with more valuable assets on a property can usually afford the multiple high quality cameras, whereas a smaller business with smaller or fewer facilities that may not be able to afford as many cameras, actually only need the few cameras they can afford.
2. Alarm Systems: Considerations for Choosing the Right Alarm System for Your Business
Alarm systems are designed to prevent intrusion and alert you and other business stakeholders when an intrusion takes place. Alarm systems usually come in four types. Each of these system types will send an alert to a central panel about any unusual activity, which usually results in the authorities being alerted, alarms being signaled, or a human operator being reported to.
The four types of alarm systems are: wired or wireless, and monitored or unmonitored:
1. Wired Alarm System
Wired alarm systems are your basic burglar alarm. This system uses a low-voltage electrical circuit that flows between two points throughout a home’s doorways and windows or other entry points. The current flows easily when doors and windows are shut. But, when a door or window is opened, the circuit is disrupted and the alarm is triggered.
Wired alarms systems have been around a while and are a common choice for most businesses since many commercial buildings already have the wiring installed. Though, if the building isn’t already wired, it may not be the most cost effective option for businesses with larger buildings.
2. Wireless Alarm System
Wireless home alarm systems are exactly what they suggest—security systems without wires.
These typically use a control panel and a series of sensors that are connected with built-in radio frequency transmitters. Once your alarm system is triggered, a signal is transmitted to the control panel and the alarm is activated.
Wireless alarms systems are good for small and medium sized businesses because they are easy to install and scale. Although the wireless equipment is more expensive than that for a wired system, they are able to connect to other security devices like cameras and mobile phones for a more accessible and complete security system.
3. Monitored Alarm System
A monitored system usually has a trusted professional looking out for you. These systems not only alert you when an emergency happens, they also notify the monitoring center operators to send emergency services.
A monitored alarm system is good for medium and large companies that may not be able to address the alarm themselves in the event it is triggered, but do have the budget for the service.
4. Unmonitored Alarm System
Unmonitored systems rely on you or someone near your home to alert the authorities of an emergency. They use audible and visual alarms are triggered whenever your system is tripped, but a monitoring center is not notified to dispatch help. They are typically a cheaper option compared to monitored systems.
An unmonitored alarm system works for smaller organizations, for whom the cost of a monitored alarm system may be out of price range, and have the ability to respond to the alarm themselves.
However, unmonitored systems don’t provide the same level of protection as monitored systems because even if you have alarm alerts sent directly to your phone, you may be unable to respond due to bad cellular reception, or because you’re away from your phone.
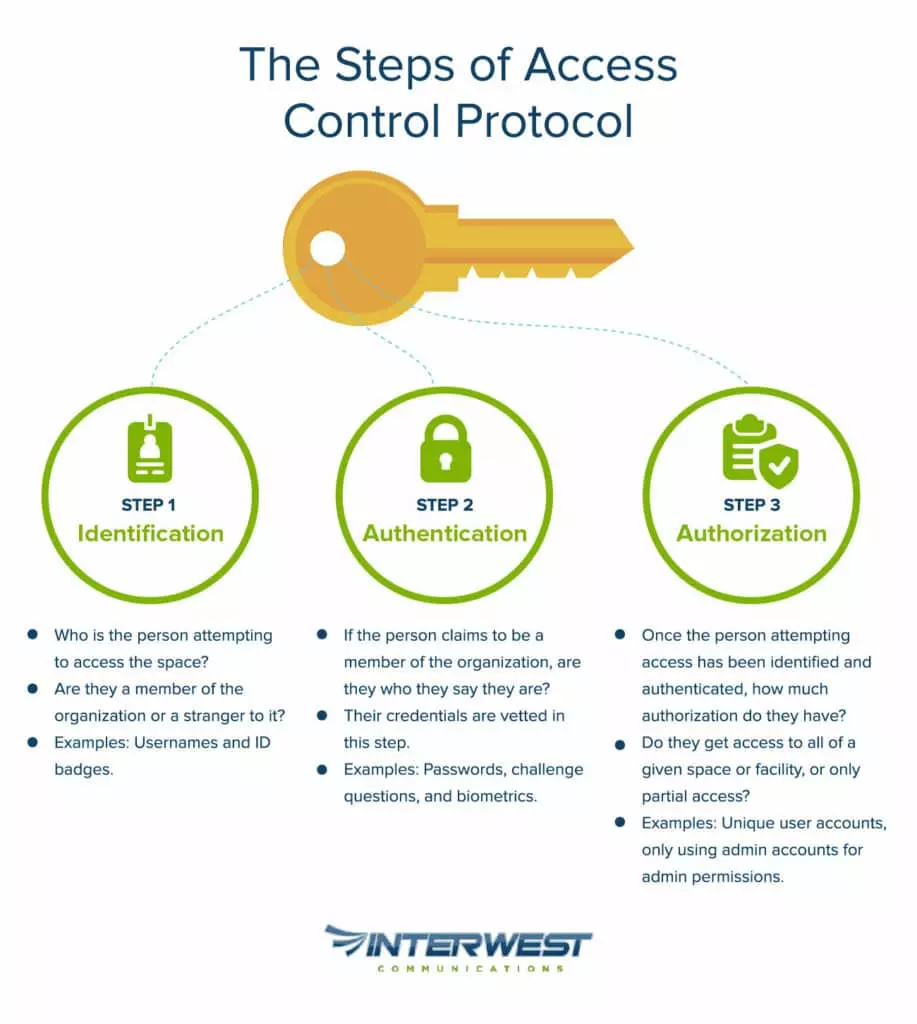
3. Access Control
Access control systems are the security practices and technology that restrict access to businesses’ data, property, and assets. They are important to mitigate the risk of unauthorized access and loss of property and sensitive information, and damages to businesses. Any sized organization benefits from access control to protect either physical or digital properties.
Types of Access Control:
Access control is divided into categories based on both implementation and function. Types of access control systems can be categorized based on the platform that they operate on.
1. On-Premise Access Control Systems
Also known as locally hosted access control, on-premise systems are installed on servers and devices that are managed on site. These systems can only be physically accessed on the premise. The benefit of this system is the level of customization and control an organization has over the system, but it is limited by their IT capabilities.
2. Web-Based Access Control Systems
Also known as cloud-based access control, web-based systems store user permissions on the web, rather than in physical devices, enabling administrators to view, manage, and control permissions from anywhere. They also automate updates and have options for vacations and other conveniences, all for a low cost, with easy deployment.
3. Mobile-Based Access Control Systems
Mobile based systems can be managed through a smartphone, which sends an unlock code to a cloud server via wi-fi or cell signal. Using a smartphone system allows you to unlock entry points into a business from anywhere, which can be useful for granting one-time access. There are also devices that use Bluetooth or near-field communication (NFC) to unlock doors, which can be a great benefit to your security systems.
4. IoT-Based (Internet of Things) Access Control Systems
Most access control systems are now connected to the internet of things (IoT) and utilize firmware to keep things updated in real-time. The wide distribution of security protocols between many different systems will help prevent unauthorized devices from communicating on the network.
4. Network Security Systems
Protecting the information network of your business is a key part of security. Network security is important to think about for all businesses because most modern companies have some form of network. This is especially true for organizations with sensitive data to protect, like finances, insurance, and the medical field. Network security consists of many different components — each one meant to protect a component of the network.
5. Security Software
Security software is used to protect specific platforms against threats targeting them. Devices and applications can have specific vulnerabilities. Specific security software is designed to address those vulnerabilities without interfering with other operations.
These security softwares are a layer of security in a specific area, in addition to the blanket security measures. Learn more about business network security best practices by checking out Interwest’s Network & On-Premise Security Checklist for Businesses.
Choose Interwest Communications for Your Business Security, Phone, & Network Needs
The ideal type of security system for a business depends on the type of business, the size and number of facilities, and the security budget scaled to match the value of the assets being secured. Ultimately, the most effective way to secure a business is by combining multiple types of systems and scaling them to the business itself.
Interwest offers video surveillance, access control, and alarm systems to meet your business’s security needs. In addition to security, we have decades of experience with data networks and telephone systems for businesses. If you have any questions, get in touch with us, and our experts will help you get the right system for your business. Our customer support is available 24/7. Get in touch today!
